User Account Control (UAC) is a key part of Windows security. UAC reduces the risk of malware by limiting the ability of malicious code to execute with administrator privileges. This article describes how UAC works and how it interacts with the end-users.
With UAC, each application that requires the administrator access token must prompt the end user for consent. The only exception is the relationship that exists between parent and child processes. Child processes inherit the user's access token from the parent process. Both the parent and child processes, however, must have the same integrity level.
Windows protects processes by marking their integrity levels. Integrity levels are measurements of trust:
Applications with lower integrity levels can't modify data in applications with higher integrity levels. When a standard user attempts to run an app that requires an administrator access token, UAC requires that the user provides valid administrator credentials.
To better understand how this process works, let's take a closer look at the Windows sign in process.
The following diagram shows how the sign in process for an administrator differs from the sign in process for a standard user.
By default, both standard and administrator users access resources and execute apps in the security context of a standard user.
When a user signs in, the system creates an access token for that user. The access token contains information about the level of access that the user is granted, including specific security identifiers (SIDs) and Windows privileges.
When an administrator logs on, two separate access tokens are created for the user: a standard user access token and an administrator access token. The standard user access token:
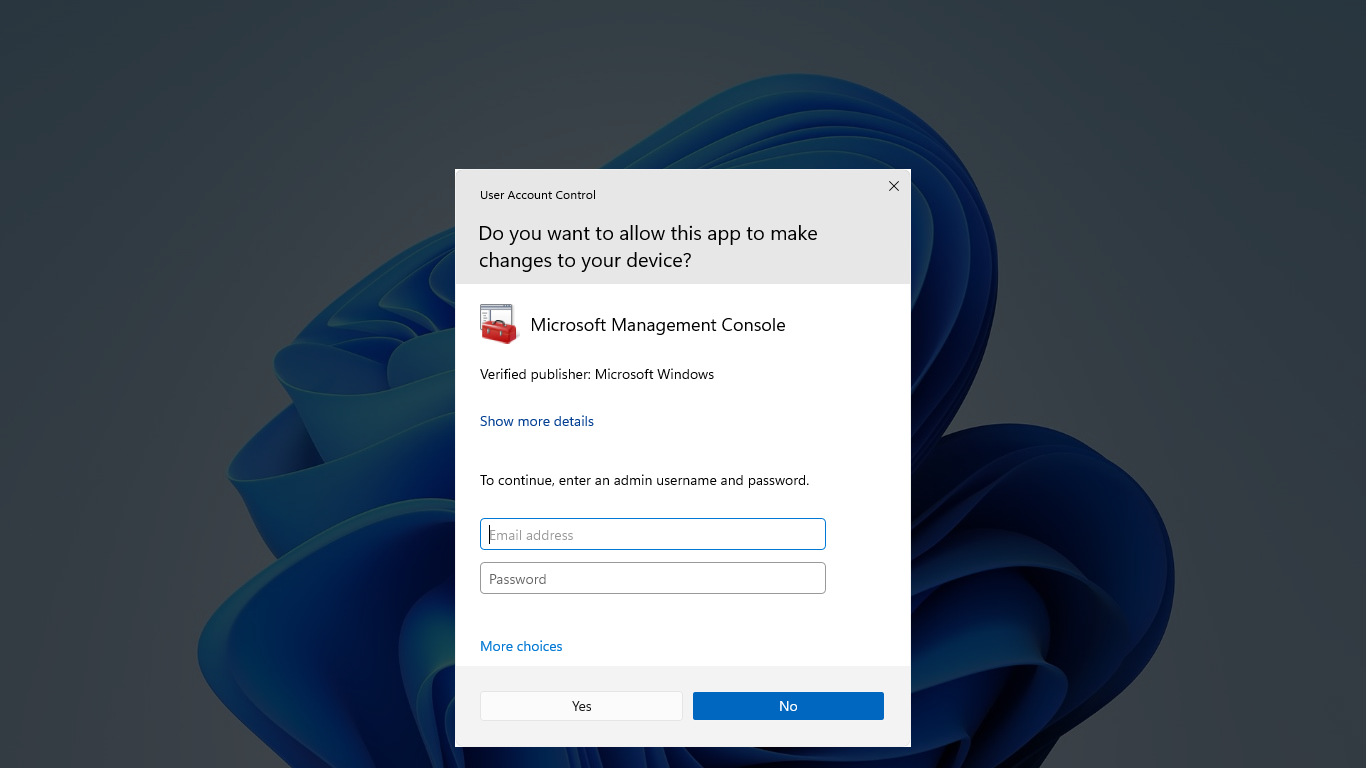
A user that is a member of the Administrators group can sign in, browse the Web, and read e-mail while using a standard user access token. When the administrator needs to perform a task that requires the administrator access token, Windows automatically prompts the user for approval. This prompt is called an elevation prompt, and its behavior can be configured via policy or registry.
When UAC is enabled, the user experience for standard users is different from administrator users. The recommended and more secure method of running Windows, is to ensure your primary user account is a standard user. Running as a standard user helps to maximize security for a managed environment. With the built-in UAC elevation component, standard users can easily perform an administrative task by entering valid credentials for a local administrator account.
The default, built-in UAC elevation component for standard users is the credential prompt.
The alternative to running as a standard user is to run as an administrator in Admin Approval Mode. With the built-in UAC elevation component, members of the local Administrators group can easily perform an administrative task by providing approval.
The default, built-in UAC elevation component for an administrator account in Admin Approval Mode is called the consent prompt.
The credential prompt is presented when a standard user attempts to perform a task that requires a user's administrative access token. Administrators can also be required to provide their credentials by setting the User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode policy setting value to Prompt for credentials.

The consent prompt is presented when a user attempts to perform a task that requires a user's administrative access token.
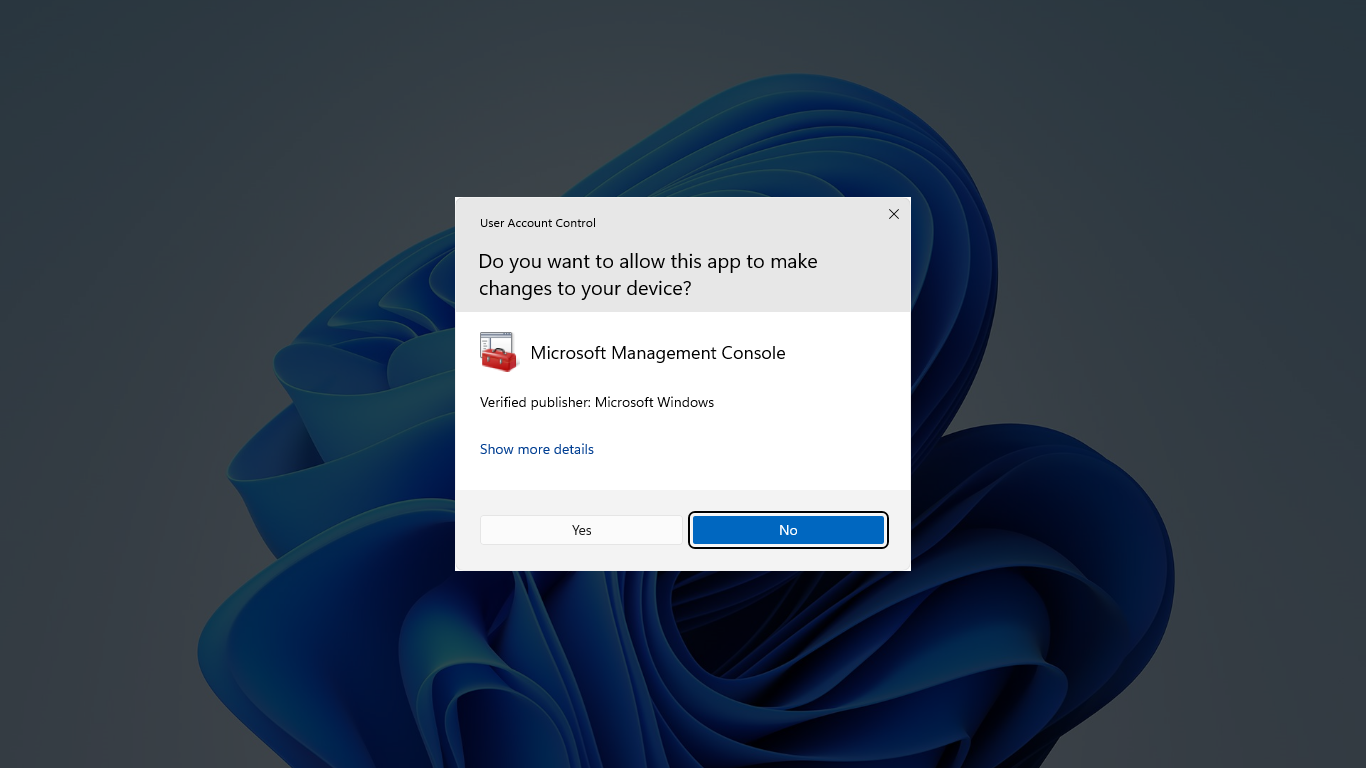
The UAC elevation prompts are color-coded to be app-specific, enabling for easier identification of an application's potential security risk. When an app attempts to run with an administrator's full access token, Windows first analyzes the executable file to determine its publisher. Apps are first separated into three categories based on the file's publisher:
The elevation prompt color-coding is as follows:
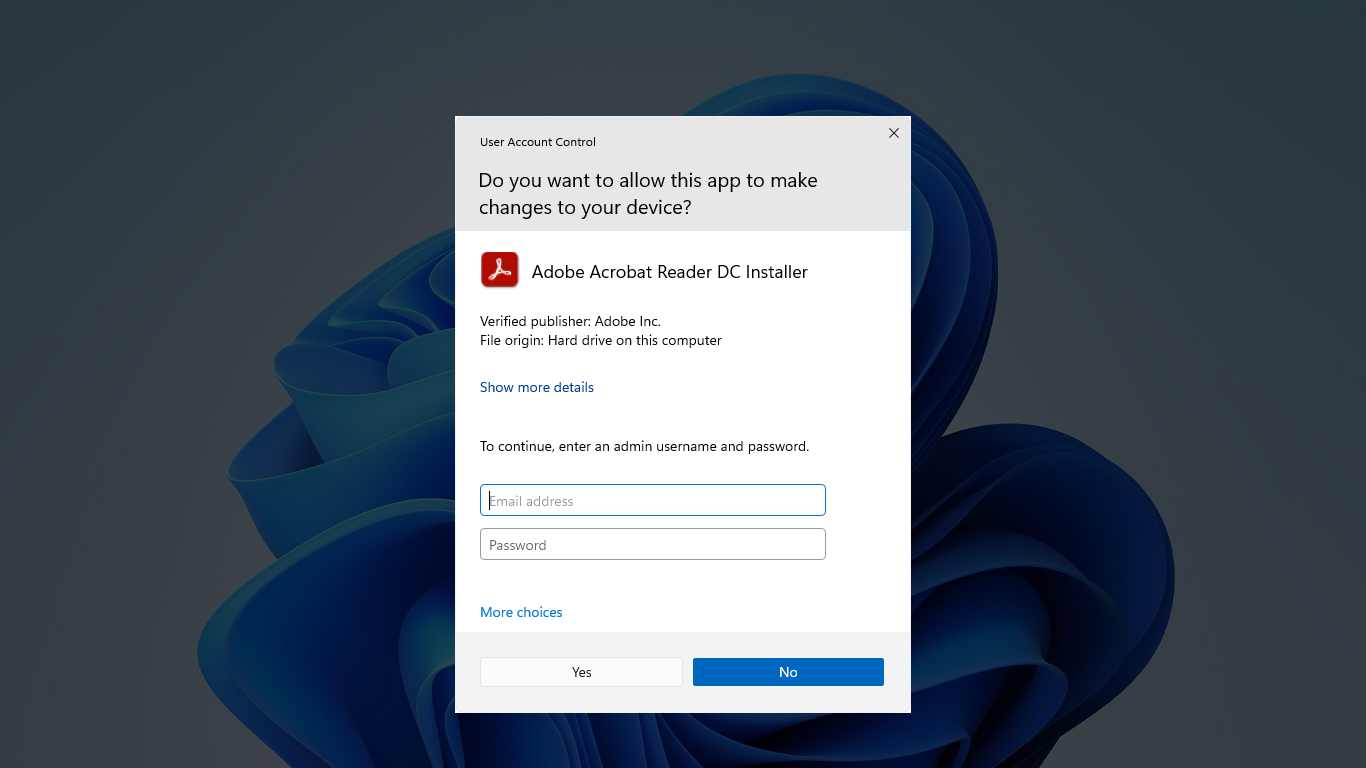
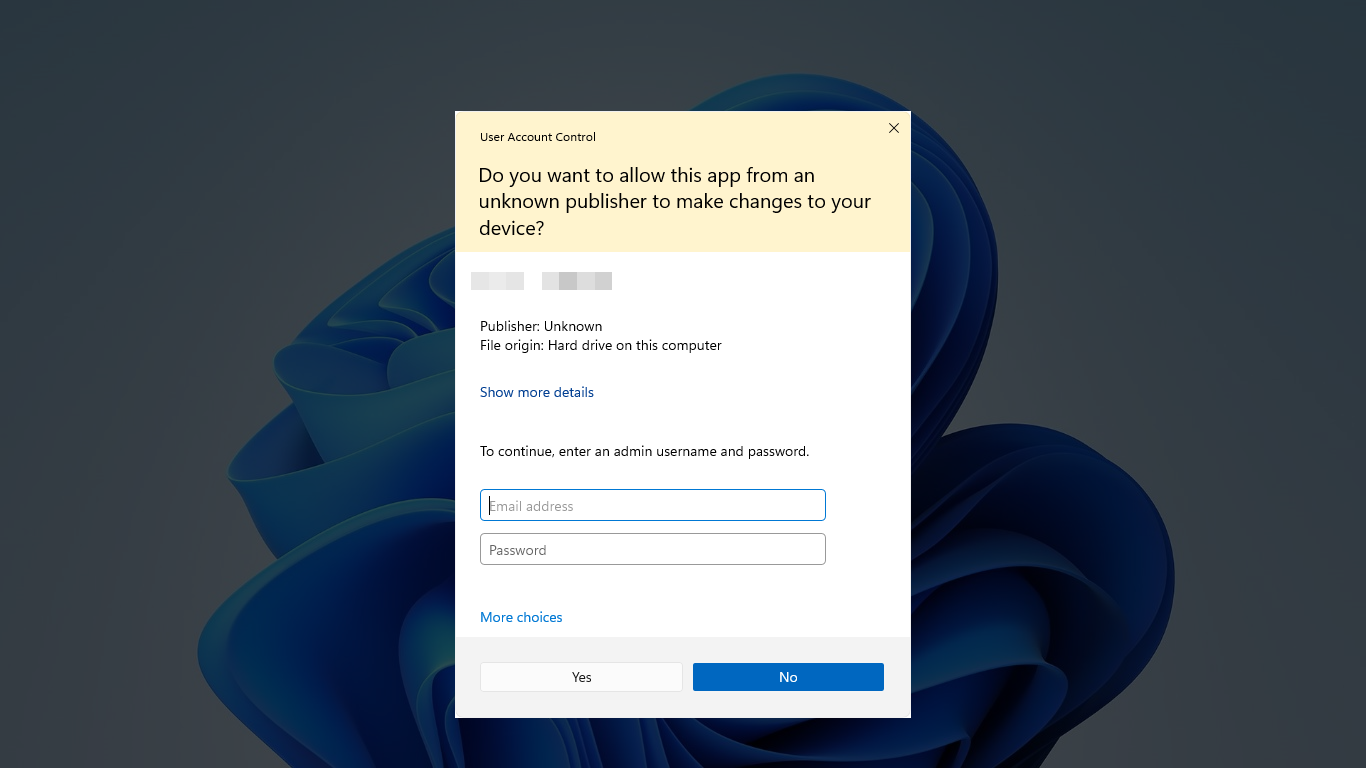
Some Control Panel items, such as Date and Time, contain a combination of administrator and standard user operations. Standard users can view the clock and change the time zone, but a full administrator access token is required to change the local system time. The following is a screenshot of the Date and Time Control Panel item.
![]()
The shield icon on the Change date and time. button indicates that the process requires a full administrator access token.
The elevation process is further secured by directing the prompt to the secure desktop. The consent and credential prompts are displayed on the secure desktop by default. Only Windows processes can access the secure desktop. For higher levels of security, we recommend keeping the User Account Control: Switch to the secure desktop when prompting for elevation policy setting enabled.
When an executable file requests elevation, the interactive desktop, also called the user desktop, is switched to the secure desktop. The secure desktop dims the user desktop and displays an elevation prompt that must be responded to before continuing. When the user selects Yes or No, the desktop switches back to the user desktop.
Starting in Windows Server 2019, it's not possible to paste the content of the clipboard on the secure desktop. This is the same behavior of the currently supported Windows client OS versions.
Malware can present an imitation of the secure desktop, but when the User Account Control: Behavior of the elevation prompt for administrators in Admin Approval Mode policy setting is set to Prompt for consent, the malware doesn't gain elevation if the user selects Yes on the imitation. If the policy setting is set to Prompt for credentials, malware imitating the credential prompt might be able to gather the credentials from the user. However, the malware doesn't gain elevated privilege and the system has other protections that mitigate malware from taking control of the user interface even with a harvested password.
While malware could present an imitation of the secure desktop, this issue can't occur unless a user previously installed the malware on the PC. Because processes requiring an administrator access token can't silently install when UAC is enabled, the user must explicitly provide consent by selecting Yes or by providing administrator credentials. The specific behavior of the UAC elevation prompt is dependent upon security policies.
The following diagram details the UAC architecture.
To better understand each component, review the following tables:
| Component | Description |
|---|---|
| User performs operation requiring privilege | If the operation changes the file system or registry, Virtualization is called. All other operations call ShellExecute. |
| ShellExecute | ShellExecute calls CreateProcess. ShellExecute looks for the ERROR_ELEVATION_REQUIRED error from CreateProcess. If it receives the error, ShellExecute calls the Application Information service to attempt to perform the requested task with the elevated prompt. |
| CreateProcess | If the application requires elevation, CreateProcess rejects the call with ERROR_ELEVATION_REQUIRED. |
| Component | Description |
|---|---|
| Virtualization | Virtualization technology ensures that noncompliant apps don't silently fail to run or fail in a way that the cause can't be determined. UAC also provides file and registry virtualization and logging for applications that write to protected areas. |
| File system and registry | The per-user file and registry virtualization redirects per-computer registry and file write requests to equivalent per-user locations. Read requests are redirected to the virtualized per-user location first and to the per-computer location second. |
The slider never turns off UAC completely. If you set it to Never notify, it will:
In order to fully disable UAC you must disable the policy User Account Control: Run all administrators in Admin Approval Mode.
Some Universal Windows Platform apps may not work when UAC is disabled.
Because system administrators in enterprise environments attempt to secure systems, many line-of-business (LOB) applications are designed to use only a standard user access token. As a result, you don't need to replace most apps when UAC is turned on.
Windows includes file and registry virtualization technology for apps that aren't UAC-compliant and that requires an administrator's access token to run correctly. When an administrative app that isn't UAC-compliant attempts to write to a protected folder, such as Program Files, UAC gives the app its own virtualized view of the resource it's attempting to change. The virtualized copy is maintained in the user's profile. This strategy creates a separate copy of the virtualized file for each user that runs the noncompliant app.
Most app tasks operate properly by using virtualization features. Although virtualization allows most applications to run, it's a short-term fix and not a long-term solution. App developers should modify their apps to be compliant as soon as possible, rather than relying on file, folder, and registry virtualization.
Virtualization isn't an option in the following scenarios:
An app manifest is an XML file that describes and identifies the shared and private side-by-side assemblies that an app should bind to at run time. The app manifest includes entries for UAC app compatibility purposes. Administrative apps that include an entry in the app manifest prompt the user for permission to access the user's access token. Although they lack an entry in the app manifest, most administrative app can run without modification by using app compatibility fixes. App compatibility fixes are database entries that enable applications that aren't UAC-compliant to work properly.
All UAC-compliant apps should have a requested execution level added to the application manifest. If the application requires administrative access to the system, marking the app with a requested execution level of require administrator ensures that the system identifies this program as an administrative app, and performs the necessary elevation steps. Requested execution levels specify the privileges required for an app.
Installation programs are apps designed to deploy software. Most installation programs write to system directories and registry keys. These protected system locations are typically writeable only by an administrator in Installer detection technology, which means that standard users don't have sufficient access to install programs. Windows heuristically detects installation programs and requests administrator credentials or approval from the administrator user in order to run with access privileges. Windows also heuristically detects updates and programs that uninstall applications. One of the design goals of UAC is to prevent installations from being run without the user's knowledge and consent because installation programs write to protected areas of the file system and registry.
Installer detection only applies to:
Before a 32-bit process is created, the following attributes are checked to determine whether it's an installer:
The keywords and sequences of bytes were derived from common characteristics observed from various installer technologies.
The User Account Control: Detect application installations and prompt for elevation policy must be enabled for installer detection to detect installation programs. For more information, see User Account Control settings list.